May 02, 2023
The industrial landscape has never been more uncertain, or more ready for digital transformation. With the need to enable remote work and team collaboration, technologies such as Cloud, Edge and IIoT not only provide new ways to enhance business performance, but also pave the way for improved business processes and procedures. Along with safety, the most critical area to address during this change is industrial cybersecurity.
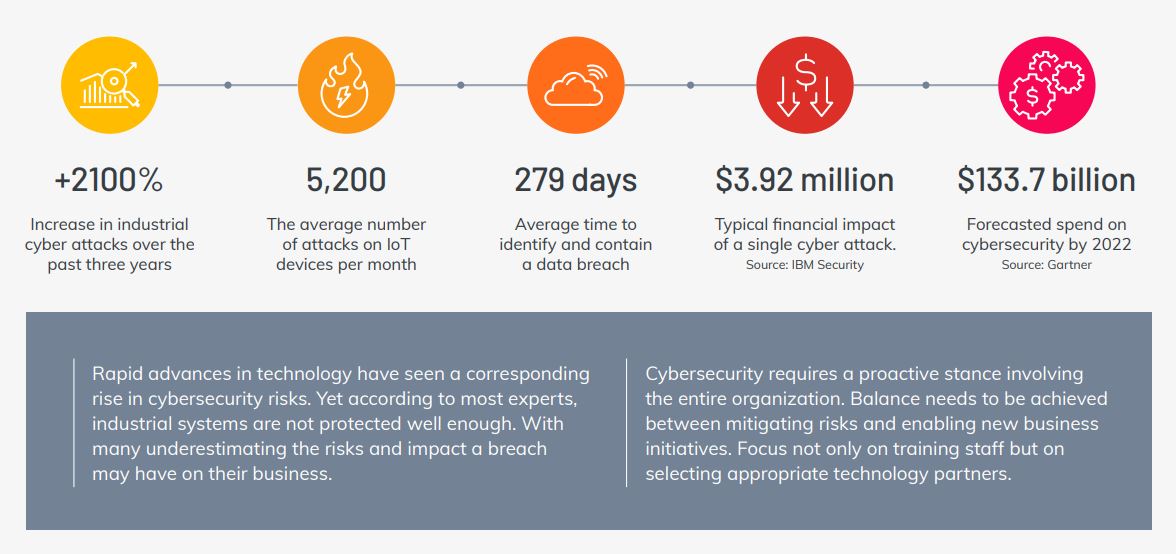
Cybersecurity by the Numbers

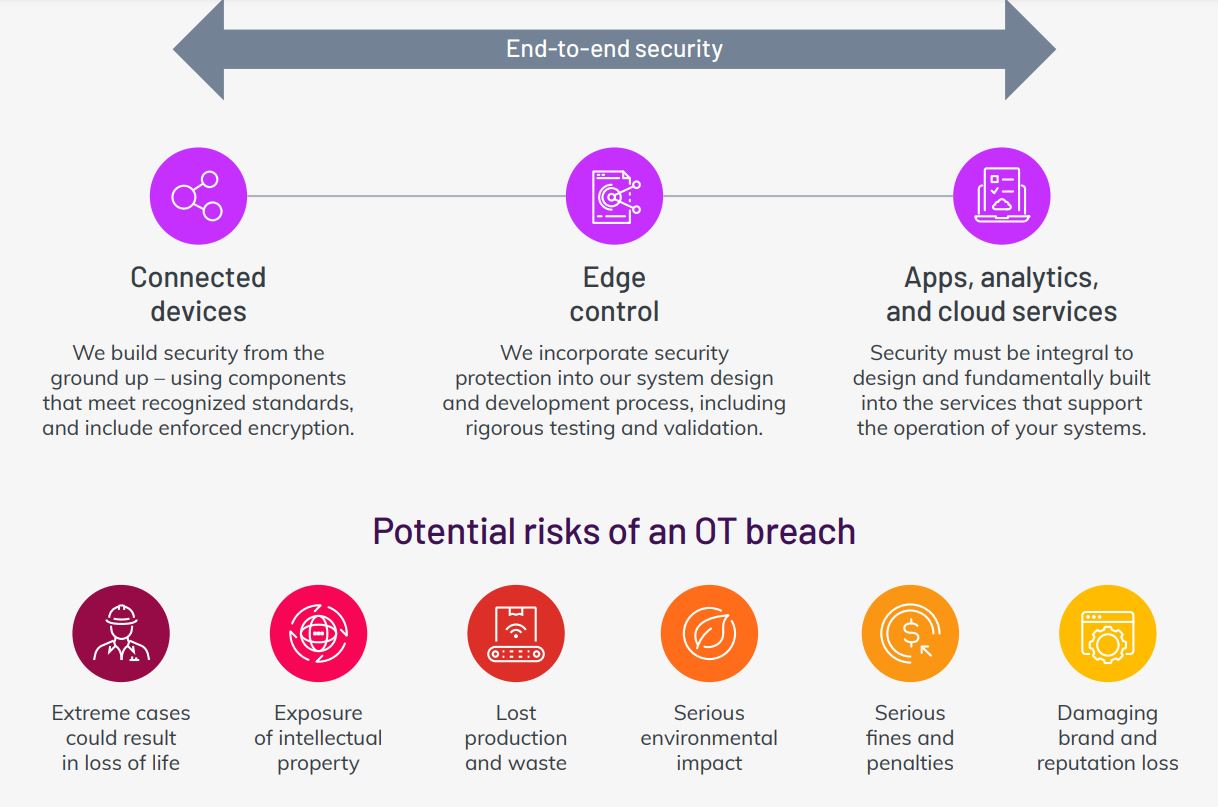
Key Security Considerations for Operational Technology
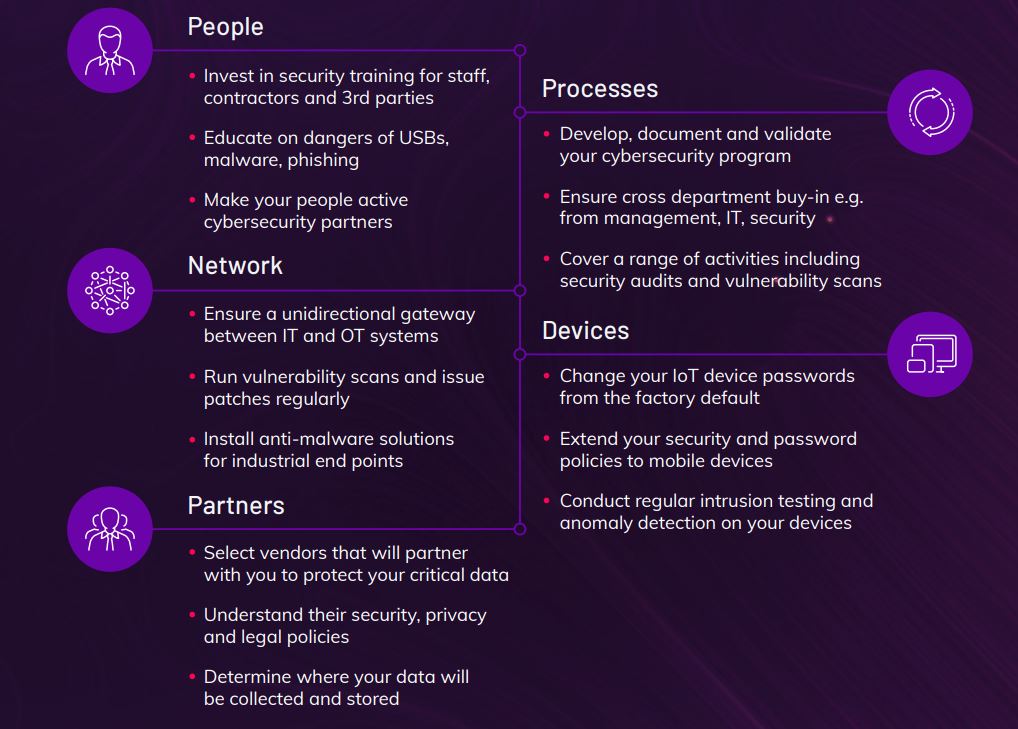
Your Cybersecurity Checklist
Cybersecurity is a multi-faceted discipline requiring a proactive approach across the business. Best-prepared businesses report a focus on the following key areas.
Cybersecurity Checklist for Your Vendor
Physical security
- Where are their cloud services physically deployed?
- Where will my data actually reside?
- Where and how will my data be captured, stored and used?
Data security
- How is your information protected – at rest and in motion?
- Does your vendor support unidirectional data transfer?
- How does your supplier deal with network outages?
Application security
- How do they handle authentication, authorization and account management?
- What is their approach to identity and access management (IAM)?
- Do they offer a flexible, scalable solution?
Continuous monitoring
- Do they have proactive monitoring and active security policies in place?
- Can they identify abnormal behavior and catch anomalous activity?
- What procedures are there to detect and isolate suspicious activity online?
Security assessments
- Do they have a proactive program of external security audits?
- How do they deal with ongoing compliance with regulations e.g. GDPR?
- Do they have a published security statement that you can read?
Projects and delivery
- Are their project delivery teams certified to global standards such as CMMi Level 5, or ISO 9001?
- Do they have a Computer Security Incident Response Team (CSIRT) ready to mobilize?
- Do they have strategic partnerships with key security experts such as Cylance or Claroty?
Source: AVEVA
There is no better time to take advantage of the IIoT and cloud technologies. Digital transformation is a journey that allows you to transform your existing automation investment into an improved way of doing business.
For more information and details, please get in contact with our Digital Transformation experts.