- Industrial Control System Security (ICS Security) includes SCADA/EMS, DCS, PLCs, RTUs, IEDs, Smart Sensors and drives, emissions controls, equipment diagnostics, AMI (Smart Grid), programmable thermostats, and building control.
- The cyber threats and attack strategies targeting automation systems are changing rapidly. Machines, systems, and subsections are becoming increasingly networked. Improvements in cost-and performance have encouraged this evolution, resulting in the adoption of “smart” technologies such as smart manufacturing, smart water, smart electric grid, smart transportation, and smart buildings. While this increases the connectivity and criticality of these systems, it also creates a greater need for their adaptability, resilience, safety, and security.
- No industrial operation is free of risk, and no network is completely secure. Without proper security measures, malfunctions or failures spread extremely fast. A cybersecurity incident can become expensive as it causes unplanned downtimes, loss of turnover and company image.
A Global Threat That We Can Control

Why do Attackers Target Industrial Control Systems?
Attackers have different motives when choosing an environment to target. When carrying out attacks, these attackers are often motivated by financial gain, political cause, or even a military objective. Attacks could be state-sponsored, or they could also come from competitors, insiders with a malicious goal, and even hacktivists.
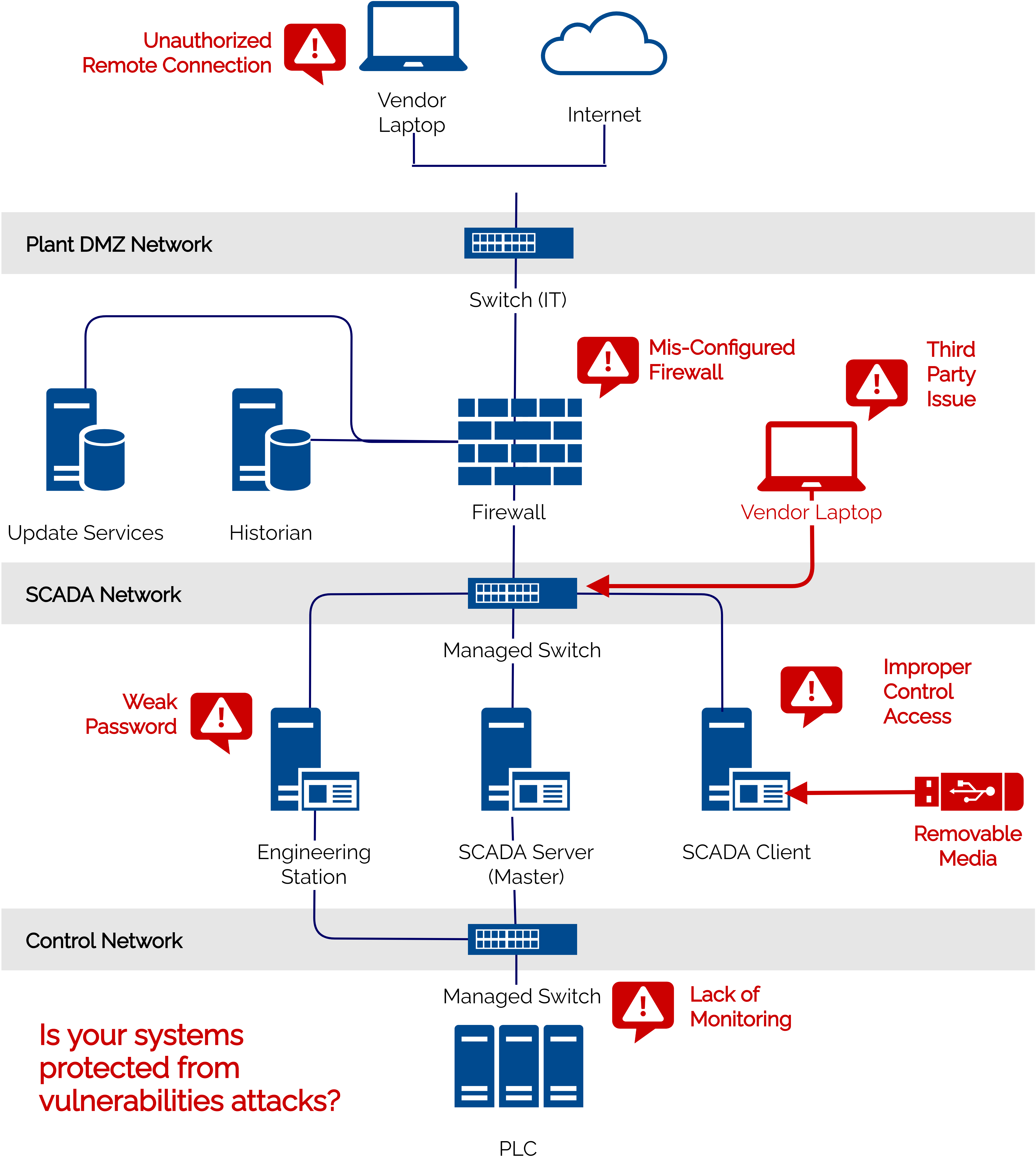
ICS environment may potentially have contain weaknesses and threats depending on their configuration and their purpose. The modern systems and tools (e.g. Internet of Things (IIoT) devices) that have been introduced to ICS environment to replace their traditional systems might introduce more vulnerabilities and loopholes for attackers to exploit.
Build a Team of Skilled Defenders
The lack of skilled defenders is the greatest risk to cybersecurity. Cybercriminals specifically target unskilled employees as an attack vector due to their lack of security knowledge. YNY Technology designs an ICS security programme and provides technical expertise with advisory to ensure the effectiveness of your security and convey the possible ICS security risks.


Establish or Enhance Governing Process
The lack of governance or process control will cause an ineffective application of security. YNY Technology enhances your governing process to ensure risk-appropriate security considerations and controls are integrated into your business process. ICS security objectives are continuously managed and assessed to lower the impact brought by ICS threats.
Right Systems with Integrity Assurance
Lack of technical security control or mechanisms will disrupt critical or real-time operations, and the theft of operational information. Adversaries target vulnerable OT networks to gain access to the control system to steal the artifacts that supply insight into your operations or prevent the operator or engineer from issuing any controls. YNY Technology helps to identify the security weaknesses in your existing OT network and system and provide protection to minimize the impact of system availability and integrity.


Certified with IEC 62443
Implementing IEC 62443 at the OT level involves a holistic approach, considering both technical and organizational aspects to secure industrial control systems effectively. IEC 62443 addresses cybersecurity in the context of Operational Technology (OT) systems, particularly industrial automation and control systems (IACS). The series provides a comprehensive framework to secure OT environments, recognizing the unique challenges and requirements of these critical systems. With our certified team, YNY Technology helps organizations determine the appropriate security levels for different components and systems within their OT environment.
Cyber Security Solution We Can Provide
People
- Consultancy
- Awareness and Training
Process
- Governance
- Compliance
- Risk Management and Assessment
- Continuous Monitoring and Maintenance
Technology
- Vulnerability Assessment and Penetration Testing
- Host and network device configuration assessment and hardening
- Network and Endpoint Protection
Comprehensive Solutions to Reduce Risk and Create Value
People
YNY Technology provides advisory and OT defense consultation to help you identify the resources needed to design, implement or practice security initiatives to improve security posture of your critical infrastructure, by offering cyber defense consultation in design and integration of security products.
YNY Technology helps you prepare for and design an ICS security programme and network architecture compliant with industry-recognized framework, before the commissioning stage to ensure effectiveness of the application of security and, within time and cost estimates. ICS security training, an integral part of the ICS security programme enables you to gain insight into ICS security risks and how they align with your business objectives.
Process
YNY Technology assess or establish a management system, the process measures with Governance, Risk management, and Compliance (GRC) comply the standards or guideline, not limited to IEC-62443, National Institute of Standards and Technology (NIST) and CSA Cyber Security Code of Practice (CCoP).
By implementing a management system, the level of ICS security risks is determined and allow the CII owner to dedicate adequate action and resources to address the root cause that could lead to undesired business consequences.
Technology
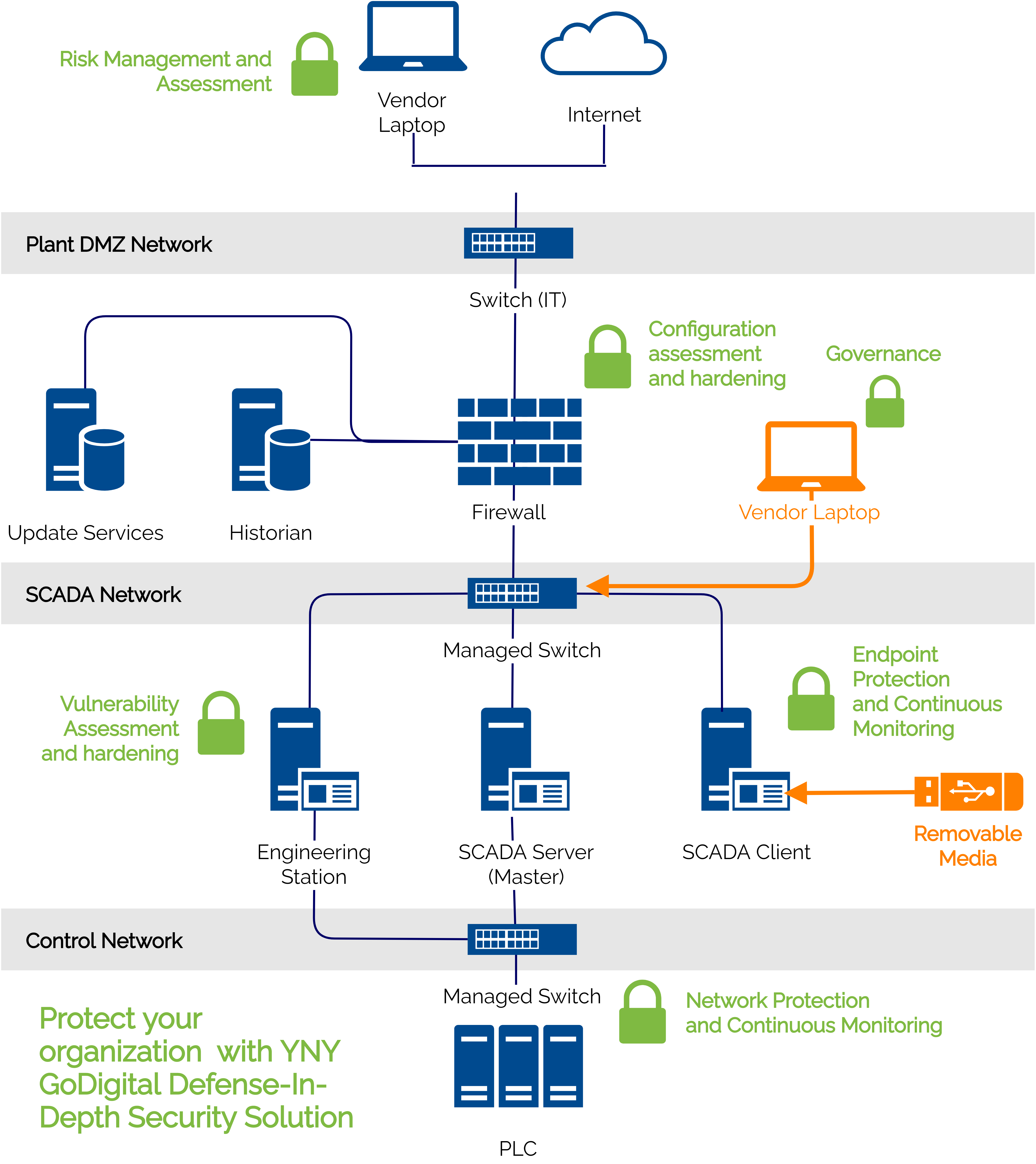
YNY Technology helps to implement technical security control or mechanisms to reveal the real vulnerabilities and reduce the ICS security risk by removing potential attack vectors and reducing the attack surface.
By implementing the security control, we help identify and confirm all possible vulnerabilities, ensure that host and network device security configurations are configured based on policy and firewall, implement secured DMZ, firewall, Intrusion Detection System (IDS), endpoint security and so forth to provide maximum protection against potential the attacks.
We Provide ICS Security Health Check
ICS Security health check helps to identify local and remote OT devices undiscovered in your asset list and detect security blind spots that existed on the device discovered. ICS risks are evaluated to help you to identify ICS threats relevant to your current environment and able to focus on the implementation of effective security control measures.